CYBERCRIME: How to Avoid 5 Common Cybercrimes?

As our world becomes increasingly digital, cybercrime poses a significant danger to both individuals and businesses alike. These crimes come in various forms, all aimed at compromising your personal or sensitive information. From sneaky phishing attempts to devastating ransomware assaults, the threats are diverse and ever-evolving. In this discussion, we will shed light on five common cybercrimes and offer practical advice to help you safeguard yourself against them. Have you ever heard of an artist thief who swipes your belongings without ever stepping foot in your home? Well, cybercriminals pull off a similar feat, except they are after your online treasures-like your passwords and credit card information. Sometimes, they will even hijack your computer with a clever hack. You can get more guides about the relevant topics by visiting the Spotipro(Spotify Premium Mod Apk Download For Tv).
It’s called cybercrime, just like being robbed in the digital realm. There are steps to protect your digital assets online, just as you keep your valuable belongings in a very confidential and highly secure safe or locker. In the realm of digital security, the year 2023 was a wake-up call as the average global cost of data breaches shot up by 15%, hitting a staggering $ 4.45 million. Shockingly, only about half of businesses are gearing up to invest more in cybersecurity. With cyber crooks constantly on the lookout for fresh targets, it’s a wonder how long companies can hold out without beefing up their defenses. The consequences of inaction are severe, underscoring the urgent need for robust cybersecurity measures.
In this article, we will discuss five common cybercrimes these digital bandits commit and offer some savvy, practical tips for shielding yourself and your data online in 2024. These tips are designed to be easily implemented, empowering you to take control of your digital security.
Types of Cybercrime
As cybercrime evolves, so does remote work, which is exacerbated by rising security threats. Weak security measures make it increasingly simple for hackers to exploit vulnerabilities, gain access to devices, steal sensitive information, launch phishing attacks, and carry out a host of other criminal activities.
It involves tricking individuals into revealing sensitive information such as passwords, credit card numbers, or personal information by posing as a trustworthy entity in digital communication. This is often done through deceptive emails, websites, or messages. To protect yourself, always verify the source of the communication, avoid clicking on suspicious links, and use strong, unique passwords for each of your accounts.
Malicious software is designed to disrupt, damage, or gain unauthorized access to computer systems or data. Examples include viruses, worms, Trojans, ransomware, and spyware. Malware can be used to steal data, spy on users, and extort money.
It occurs when someone steals another person’s personal information, such as their social security number, credit card details, or bank account information, and uses it for fraud purposes. This can lead to financial loss, damage to credit ratings, and other severe consequences for the victim, such as being falsely accused of crimes committed by the thief or having their relationships affected due to the thief impersonating them online.
Cyberstalking involves using the internet, social media, emails, or other digital means to harass, threaten, or intimidate someone. This can include sending unwanted messages, tracking someone’s online activity, or spreading false information about them. Cyberstalking can have severe psychological and emotional effects on victims.
Data breaches occur when unauthorized individuals gain access to sensitive or confidential information, financial records, intellectual properties, or trade secrets. They can result from hacking inside threats or accidental exposure and can have significant financial and reputational consequences for the affected organization.
These are just examples of many types of cybercrimes, and the landscape is constantly evolving as technology advances and cybercriminals develop new tactics.
Phishing
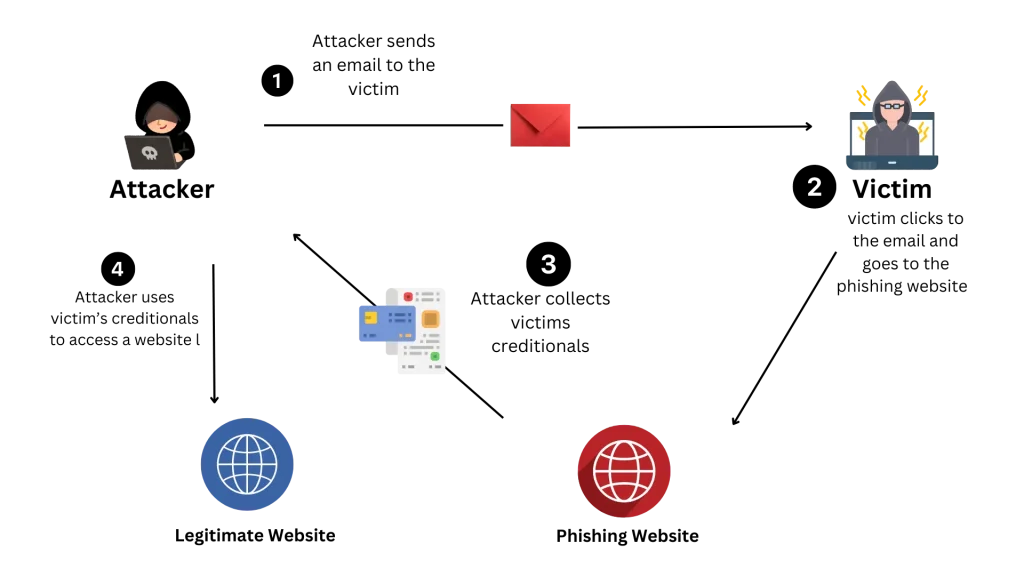
Phishing is not just a cyberattack; it’s a grave threat that can lead to severe consequences. Scammers employ cunning strategies to trick individuals into revealing sensitive information like passwords, credit card numbers, or personal identification. For instance, they might send an email posing as your bank, requesting you to update your account details. Or they might create a fake social media account of a friend and send you a message soliciting your personal information. These attacks are rampant through email, instant messaging or counterfeit websites designed to resemble legitimate ones.
They do this to either make a quick buck, sell the info on shady online markets, or gain a competitive edge. These phishers are skilled—they will impersonate someone you know and trust, like a coworker, friend, or even someone in authority, to make their scam seem authentic. For example, a scammer might send an email posing as your boss, asking for your login credentials. Initially, they will reach out through email, phone calls, texts or even social media chats, and lately, they have been getting crafty with WhatsApp, too. Some pose as fake employers offering too good-to-be actual jobs to capture your personal information.
Understanding the gravity of phishing attacks is paramount. Scammers are now leveraging advanced AI to create emails and documents that are virtually indistinguishable from legitimate ones, often without the typical signs of a scam, such as typos or poor translations. This underscores the immediate need for unwavering vigilance and the critical importance of double-checking any unexpected messages that request your information. By doing so, you can take charge of your online security and fortify yourself against these deceptive tactics. The consequences of falling victim to a phishing attack can be severe, ranging from financial loss to identity theft. It’s not just about protecting your personal information but also safeguarding your financial well-being and reputation.
Preventions:
- Email Filters and Anti-Phishing Tools: Set up email filters and Anti-phishing tools to automatically scan incoming emails for any sneaky stuff and block anything suspicious before it even hits your inbox. These tools are highly effective in preventing phishing attacks, giving you peace of mind and confidence in your online security.
- Multifactor Authentication: Strengthen your Account security with MFA, especially for those holding sensitive data. MFA makes it so you need more than just a password to get in, adding a layer of protection. It’s a simple yet powerful tool that empowers you to take control of your online security.
- Stay Updated: Keep all your gadgets and software updated with the latest patches and fixes. Outdated tech is like an open invitation for hackers, so be aware of their tricks and don’t let them in.
- Take personal responsibility for Your online security. Train yourself and your team to double-check any unusual or unexpected requests, especially if they involve personal information or money. Remember, it’s better to be cautious than to be a victim. By being vigilant, you can play a significant role in preventing phishing attacks.
- Email Filtering Solutions: Use email filtering solutions to filter through your emails and separate any dark ones. This reduces the risk of being robbed digitally.
- Implement DMARC: Set up DMARC, an email authentication protocol that helps prevent tricking attacks. It stops cyber crooks from imitating your domain in phishing emails. In addition, with a DMARC MSP’s help, you can monitor your email security and tighten things up if needed.
Malware Attacks
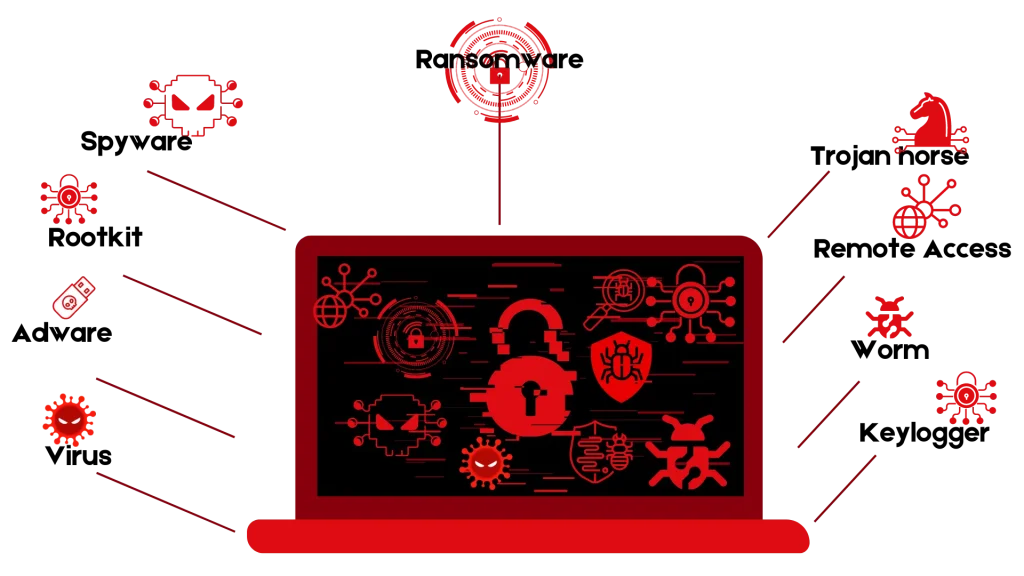
Malware attacks are not a matter to be taken lightly. They persist as one of the most widespread and easily exploitable methods for infiltrating systems. Hackers prefer malware for its speed, efficiency, and straightforward management. These attacks involve forcefully implanting hostile software into various digital entities, such as software, iOS devices, program versions, websites, or web browsers. The repercussions can be dire, ranging from pilfering sensitive data to disrupting regular operations. Each type of malware presents a unique threat, from covert data theft to complete systems lockdown. It’s crucial to stay updated against these evolving cyber threats to safeguard your digital assets and operations.
The facets of malware encompass a range of threats, including viruses, trojan horses, spyware, adware, worms, rootkits, ransomware, keyloggers, botnets and logic bombs. Each of these types poses a unique threat, from clandestine data theft to outright systems lockdown. For example, a virus can corrupt your files, a trojan horse can give hackers remote access to your system, and ransomware can encrypt your data and demand a ransom for its release. Maintaining up-to-date knowledge and defenses against these evolving cyber threats is paramount for both individuals and organizations to safeguard their digital assets and operations. You can also have the best ways to optimal data backup options here at Guides.
Preventions:
- Data validation and sanitization: Double-check and clean up any information users enter into your system before you use it. It means your system accepts only the commands you prespecified.
- Parameterized and Prepared Statements: Well, if we’re talking about databases, use parameterized and prepared statements. The system treats them as plain old data from a user command, not sneaky bits of code that cause trouble.
- Content Security Policy: Content Security Policy headers or CSPs are used in web applications. These tools will allow you to command your browsers exactly where they are allowed to grab content from. If scammers are trying to load stuff from unreliable sources, your CSPs will put a stop to it.
Identity Theft
Have you ever heard of Identity theft? It’s not like getting robbed physically, but the sneaky crime happens when someone steals your personal information and uses it for their benefit. Imagine someone is playing tactics to be you, reaching out to your bank accounts, committing crimes, or even shopping online—all under your identity. It’s a chilling thought! In this pro-tech era, nothing is to be taken for granted because everything is under control. In this blog post, we will break down what identity theft is all about, how to spot it, and most importantly, how to protect yourself against it. The implications of identity theft can be far-reaching, from financial loss to damage to your personal and professional reputation. It’s not just about protecting your personal information but also safeguarding your financial well-being and reputation.
Preventions:
- Check Your Credit Report: Check your credit card information and bank account details regularly to spot any unauthorized activity or accounts opened in your name. You are entitled to a free credit report from each of the major credit bureaus annually.
- Shred Documents: Beforethrowing out any documents containing personal information, make sure to tear them correctly to prevent dumpster diving thieves from getting their hands on them.
- Secure your devices: Install and regularly update antivirus software on your computer and mobile devices. Also, enable firewalls and use encryption whenever possible to protect your data.
Cyberstalking
Cyberstalking, a severe issue that can affect anyone, is a danger we must all be aware of in today’s digital age, where our online presence is significant. Easy access to our privacy and making us feel unsafe is genuinely alarming. Cyberstalking, which involves the use of digital means to harass, intimidate, or threaten someone, is disturbing and should never be underestimated. It can manifest in various ways, such as sending unwanted messages, monitoring someone’s online activity without their consent, or even using technology to track someone’s movement in the physical world. This includes being cautious about what personal information we share and setting strict privacy settings on our social media accounts. If you ever feel like you are being cyberstalked, it’s of utmost importance to reach out for help and support without delay. Remember, there are people and resources available to assist you in these situations, ensuring your safety and peace of mind.
Preventions:
- Trust your instinct: If you feel uncomfortable or suspicious about someone’s online behavior towards you, trust your instincts and take action to protect yourself. You have the power to block or report individuals who engage in harassing or stalking behavior, thereby taking control of your online safety.
- Monitor online Presence: Regularly monitor your online presence by searching your name and reviewing the information available about you online. If you find any concerning content, take steps to remove or address it.
- Limit location sharing: turn off location services on social media apps and other platforms when they are not necessary, and be mindful of sharing your location publicly.
- Seek support: If you believe you are being cyberstalked or harassed online, don’t hesitate to seek support from your friends, family, or relevant authorities. Keep evidence of the behavior, such as screenshots or messages. To report the incident, you can visit the ‘Help Center’ on the platform where the incident occurred or contact your local law enforcement agency. They will guide you through the process and ensure your safety. Remember, reporting is crucial in preventing further incidents.
Data Breaching
Data breaching is like unwelcome guests intruding on a party, except instead of enjoying dinner, they insert their noses into our personal information. It happens when illegal persons get access to personal information like our passwords, financial details, or even our addresses without our consent. It’s like having someone hunt through your mailbox or peek into your diary—it’s horrible.
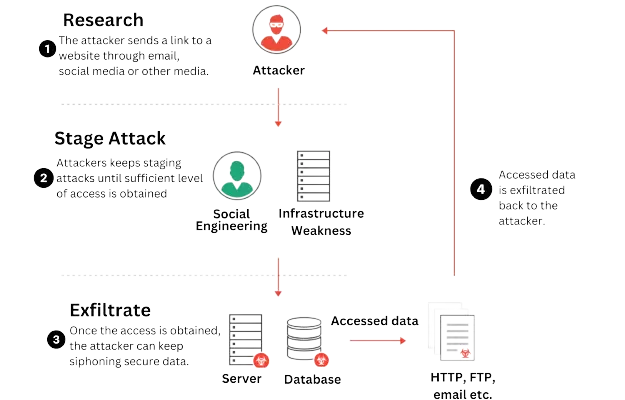
Data breaches can happen for various reasons, from cybercriminals exploiting security susceptibilities to accidental leaks by companies. They can have serious consequences, including financial scams and insecurities about identity theft, organizations responsible for safeguarding our data. That’s why it’s essential to stay vigilant, use strong passwords, and keep an eye out for any suspicious activity that could signal a breach. After all, our data deserves to be treated like VIPs, Not left for stalkers to misuse.
Preventions:
Preventing data breaches is like installing a security system for our digital lives. It’s all about protecting our sensitive data from unauthorized scammers. The best ways to do this practice are given below:
Cyber Hygiene: Cyber hygiene involves regularly updating software and using unique and strong passwords for every account. It’s crucial to be cautious about how we share our personal information while online.
Cybersecurity Measures: For businesses, implementing robust cybersecurity measures, such as encryption and multifactor authentication, can help fortify their defenses against potential breaches.
Educating Employees: Additionally, educating employees about cybersecurity best practices and conducting regular security audits can go a long way in preventing data breaches before they occur. By taking these preventive measures to protect our data, we can reduce the risk of falling victim to cybercrime and keep our digital lives safe and secure.
Conclusion
Cybercrimes are like stubborn weeds that persist despite our best efforts. But fret not. We have potent tools and tactics to safeguard our data from these criminals. One such tool is DMARC, a superhero for your email security. Services like PowerDMARC can simplify its setup, providing you with a sense of security in your data protection.
When it comes to security, social engineers can be sneaky, tricking people into giving up sensitive information. It’s easier to fool a person than a computer, so as a business owner, don’t forget to put some effort into training your team and running surprise drills. Your skillful team is the wall against cyber villains, and their role is invaluable.